Posted by Lee Elkasri on 26th May 2016
Special post: Security Alert for our Ubiquiti® customers
There has been virus activity detected in some Ubiquiti devices that have the airOS M installed through custom scripting. Devices were infected through SSH port 22 on radios with out-of-date firmware and whose HTTP (port 80)/HTTPS (port 443) interface was exposed. Most reports suggest that the devices are reset to factory defaults and still operational, although inaccessible.
To check your devices and remove any malware, please download the following Ubiquiti tools, which will also upgrade your device to airOS® v5.6.5, and will disable custom script usage:
PC: http://www.ubnt.com/downloads/XN-fw-internal/tools/CureMalware-0.8.jar.
Android: https://play.google.com/store/apps/details?id=virusfixer.ubnt.com.ubntvirusremoval
The following devices are NOT affected:
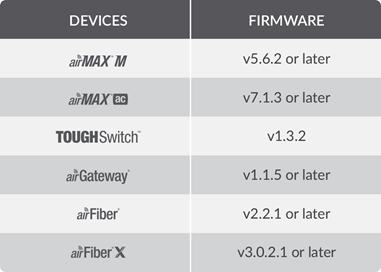
Should our customers have any questions, please contact WLANMall or Ubiquiti Support.
